Avast Secureline Vpn For Mac & Subscription Ended Message In Error
In what will be our final chapter of our ‘Introduction to ‘ course, I will tell you something beyond the usual tech jabber on VPN. I’ll cover some technical and legal issues which are directly related to the use of VPN and provide some practical advice in the end. Technical aspects An observant reader might recall that I put a considerable emphasis on correct implementation, setup and use of all kinds of VPN in the of our series. Even the most reliable version of the protocol is worthless if used improperly.
Feb 7, 2019 - Avast Secureline offers both free (7-day trial) and paid versions. Let's find out in this Avast Secureline VPN review. They do, however, have a Twitter account where users can send in direct messages. Just as sophisticated and simple as using the service on a PC or Mac. Netflix VPN streaming error. Once your Avast protection will start expiring, you will start getting the following pop-up notifications with the message ‘Your Avast expires in X days – choose your protection‘. You basically need to select between the ‘Standard protection‘ (Free Antivirus) and ‘Complete protection’ (Internet Security).
All VPN solutions we have previously covered had one thing in common: they include open-source implementations, which should be easier to check for vulnerabilities. However, in reality, there are other issues and peculiarities, besides those contained in the code. VPN is not offered with our products, but we recommend a few here:. — Kaspersky Lab (@kaspersky) The most obvious problem is the occasional disconnect of VPN which, consequently, all of a sudden, routes the traffic through a public network. For instance, it may well happen when a user is connected to a public Wi-Fi network or any other available mobile network. The worst case is when the user is not notified of that and the VPN connection is not re-established automatically.
In Windows 7 and higher, Microsoft introduced the feature. If you use an alternative platform, you would need to take advantage of customized routing settings or a so-called ‘kill switch’ feature. The latter monitors the status of the VPN connection. If it is lost, the traffic is blocked, all apps running are stopped, and the stem attempts to re-establish the VPN connection. Some commercial VPN clients offer similar functionality.
What exactly is VPN? — Kaspersky Lab (@kaspersky) The second VPN leak, which is far less obvious and frequent, is related to the IPv6 protocol. Although IPv6 is still rarely used in the wild, all major operating systems have this protocol enabled by default, whereas VPN mostly uses IPv4. What may happen in this regard is the situation when IPv6 is supported on a public network, and the client may as well connect to a resource which uses the same version of the protocol, thus routing traffic to a public IPv6 network by default.
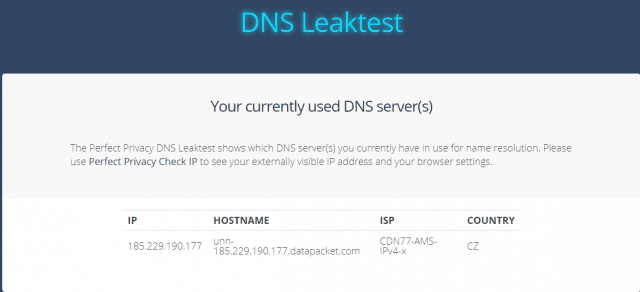
The simplest measure here would be to fully disable IPv6 support on the system level. Why are there no games for mac. Of course one can route all the traffic into the VPN, but it would require both server-side support and particular settings on the client side. Conducted in 2015, offered VPN providers a gentle nudge and they started to seek appropriate solutions for their clients. Implementations of and some of their peculiarities — Kaspersky Lab (@kaspersky) The research also cites the third issue: leaks. In the best-case scenario when a user connects to VPN, all DNS requests should not leave the VPN network and be processed by corresponding DNS servers.
Otherwise, known trusted servers like Google Public DNS or OpenDNS should be configured in the network on installation. Alternatively, one can use VPN bundled with services like.
The latter serves to encrypt and verify DNS requests/responses authenticity, which is also quite useful in many other cases. In real life, those recommendations are rarely followed, and people use DNS servers offered by the public network. Surely, the response acquired from those servers might be incorrect and even fake, which is a great opportunity for adversaries practicing farming. The collateral damage of the DNS leak would be the compromise of privacy: an outsider may find out DNS servers’ addresses, thus the name of the ISP and more or less accurate location of the user. Those using Windows are even in a graver situation. Whereas Windows 7 would try all known DNS servers one by one and wait to get a response, Windows 8/8.1 makes things faster by simultaneously sending requests to all known DNS servers on all known connections.